Migrate to Linux
Migrate to the world of Linux
TOP Reasons To Switch Over To Linux OS
The Linux project was announced by the Linux creator Linus Torvalds on August 25, 1991. With time, Linux has managed to earn a respectable place in the open source world. With other OS still struggling to provide security and reliability at the first place, here are 10 reasons to switch over to Linux.
Linux has been around for years and so as the other operating systems. The evidences, rumors and even frustrations from the tech world suggest that Linux still leads the way at personal as well as enterprise level.
Here are 10 reasons to switch over to Linux from other operating systems right now:
1. Linux is free:
Leave aside Apple, we all know how things and software at professional level work in Apple. Even Windows charges for upgrades. However, if you want to switch over to the Linux, you do not have to pay any extra cost. Yes, it’s completely free.
2. More Secure:
Ask people who use Windows. Ask how much they do not want unwanted things playing around their computers. Basically, you cannot survive without an antivirus.
On the other hand, Linux is unknown to a virus and so, antivirus as well. You do not have to pay much attention towards security and programs doing unwanted things in the background.
3. It’s easy to use:
Well, it might sound like a stupid statement but gone are those days when you needed to be a computer expert to use the Linux operating system. With time, the Linux has evolved and these days, Linux also offers great user interface like other operating systems. It just takes to come out of your closet and try your hands on this beautiful OS. Once acquainted with it, you might very well start enjoying playing around with the Linux.
4. It runs Free and Open Source Software (FOSS):
Not to be denied, you can pretty much install many of the proprietary titled software to your Windows. However, when it comes to running FOSS on Windows, its same as India building a dam in Pakistan on a river originated in China. You know what I mean. What’s so special about FOSS? Well, it’s free, easy to use, usually stable, and secure and versatile — the same things that make Linux special.
5. It’s Versatile:
Most of the popular operating system run on ‘One size fits all’ benchmark. When we talk about Linux, there are literally different versions that you can further customize to suit your needs. For example, if you are a gamer, you can simply install/ uninstall some packages to move from a DJ to a gamer level in Linux. This kind of flexibility is not offered in other OS. That’s why Linux is Versatile.
6. Compatibility:
Ah! when upgraded from lower versions to higher versions, many software need further up gradation. On top of that, there are compatibility issues with the hardware and drivers. Well, that’s not a regular case with the Linux. You can literally survive on a machine from even 90s.
7. Software repository:
Well, you do not have a particular store called app store or Android store or Windows store, where you might have to buy a professional version of a software. The Linux world has its own store and there, everything is for free. Linux recommends a compatible software automatically for you and also, you keep on getting automatic updates for free.
8. Regular Linux updates:
You do not have to wait every one year or every eighteen months for an upgraded software roll out and in the meantime keep struggling with the lacuna of your operating system, or trying to find a fix temporarily. Yes, in the Linux, you get regular updates along with the provision of short-short updates and that too for a particular package. Moreover, you do not need to restart your machine in all cases. It just happens like a fluke.Also read:
9. Drivers already included in Linux:
We have seen those times, when after installing an operating system, the next step we had to go for will be the long process of installation of drivers like wifi driver, Bluetooth driver, touchpad driver, graphics card driver, audio driver and much more. Well, that’s not the case with the Linux. Most of the drivers are supported by the Linux Kernel. That means you do not have to hunt around to find a driver. It’s more like plug n play.
10. Big Linux Community Support:
Linux community is probably the best thing Linux has seen. You are never alone. There are a plethora of forum where you will find the answers for your problem. If you think you can resolve the issue, you can also contribute towards it. Such support is still missing in other OS.
What are all the advantages of using Linux rather than Microsoft Windows?
- Cost – The most obvious advantage of using Linux is the fact that it is free to obtain, while Microsoft products are available for a hefty and sometimes recurring fee. Microsoft licenses typically are only allowed to be installed on a single computer, whereas a Linux distribution can be installed on any number of computers, without paying a single dime.
- Security – In line with the costs, the security aspect of Linux is much stronger than that of Windows. Why should you have to spend extra money for virus protection software? The Linux operating system has been around since the early nineties and has managed to stay secure in the realm of widespread viruses, spyware and adware for all these years. Sure, the argument of the Linux desktop not being as widely used is a factor as to why there are no viruses. My rebuttle is that the Linux operating system is open source and if there were a widespread Linux virus released today, there would be hundreds of patches released tomorrow, either by ordinary people that use the operating system or by the distribution maintainers. We wouldn’t need to wait for a patch from a single company like we do with Windows.
- Choice (Freedom) – The power of choice is a great Linux advantage. With Linux, you have the power to control just about every aspect of the operating system. Two major features you have control of are your desktops look and feel by way of numerous Window Managers, and the kernel. In Windows, your either stuck using the boring default desktop theme, or risking corruption or failure by installing a third-party shell.
- Software – There are so many software choices when it comes to doing any specific task. You could search for a text editor on Freshmeat and yield hundreds, if not thousands of results. My article on 5 Linux text editors you should know about explains how there are so many options just for editing text on the command-line due to the open source nature of Linux. Regular users and programmers contribute applications all the time. Sometimes its a simple modification or feature enhancement of a already existing piece of software, sometimes its a brand new application. In addition, software on Linux tends to be packed with more features and greater usability than software on Windows. Best of all, the vast majority of Linux software is free and open source. Not only are you getting the software for no charge, but you have the option to modify the source code and add more features if you understand the programming language. What more could you ask for?
- Hardware – Linux is perfect for those old computers with barely any processing power or memory you have sitting in your garage or basement collecting dust. Install Linux and use it as a firewall, a file server, or a backup server. There are endless possibilities. Old 386 or 486 computers with barely any RAM run Linux without any issue. Good luck running Windows on these machines and actually finding a use for them.
- Flexibility – You don’t have to deal with anti-piracy schemes and additional “hoop jumping”.What about not needing to assess the number of security solutions out there for Linux. Just visit the Wilders Security Forums, and you’ll see what I mean!There isn’t like 1 AV solution, or a few access control solutions (SELinux, grsecurity, etc)…In Windows, there’s like 50+ AV solutions, a whole dozen anti-malware apps, intrusion prevention, anti-this, anti-that, etc…People say this one is better, others say that one is better. In less than 10min, you’d be pretty confused as to which is the best for your needs!
TOP free Linux and open source software
Have you ever wondered what are some cool Linux softwares or tools that you must try?? Well I thought that when i was new to this world i.e. what new can i try that would ease my work?
So,here is a list of all the packages without which your system is incomplete. Many of you might be using many of them but for those who have not started using them TRY THEM NOW!!!
1.YAKUAKE (A terminal emulator)
Yakuake is a KDE drop down terminal emulator i.e it slides down from the top of the screen when a key is pressed, and slide back up when the key is pressed again.It is a feature-rich terminal application that supports skinning, split-viewing, profiles and which runs in the background without you even being aware of its presence.
2. VIM ( The text editor )
Everyone has his own pick of a text editor 

3. GIMP ( Photoshop alternative  )
)
GIMP for me personally is a good alternative that i found for photoshop in linux.It can help you create your website graphics like banners , buttons and patterns from scratch. It is a great tool to enhance and retouch your digital photoes.Also GIMP has a strong community over the internet so you can always find someone to help you when you are stuck. “Well thats the real advantage of open source community 
4. Libre office ( The free and open source office suite )
Most probably libre office comes preinstalled but for in case it does’nt you may always do it.From documents to spreadsheets to presentations and more, LibreOffice has all the tools you need to get things done.

5. Sprunge (The command line pastebin )
Pastebin is a must when we get stuck to paste our code and ask up in the community.Bored of going to the pastebin then doing the copy and paste??.Sprunge is a good alternative as a command line pastebin.After installation
To share a file, just do :
$ cat FILE | curl -F ‘sprunge==<-‘ http://sprunge.us
To pipe the output of any command execute :
$ COMMAND | curl -F ‘sprunge==<-‘ http://sprunge.us
6.Pidgin(The instant messenger)
Pidgin is the favorite instant messenger of many Linux users, and for a good reason. With support for all the popular chat protocols – Gtalk, IRC, Yahoo, ICQ, XMPP – and others (like Facebook) available via official and third-party plugins, who wouldn’t love Pidgin? It also works on Windows, and has many cool features, like custom emoticons, “Now Playing” status messages, different types of notification and buddy grouping and filtering.
7. TOR
We might pretend we don’t care or console ourselves by thinking we’ve got “nothing to hide”, but the fact is that privacy and security are extremely important, and that it’s a wise practice to be mindful of them on the Internet. Tor helps you in that mission by providing a browser and communication tools that block trackers and enable anonymized surfing.
8. Youtube-dl (The youtube downloader)
Its a pretty good command line downloader for youtube videos.You can download any video and even the whole playlists in a zippy 
9.Amarok (The music player)
Amarok serves many functions that can be used to organize a library of music into folders according to genre, artist, and album, can edit tags attached to most music formats, associate album art, attach lyrics, and automatically “score” music by keeping play count statistics.Also from version 1.4.4, Amarok introduced the integration of magnatune, a non-drm digital music store, enabling users to purchase music in Ogg, flac, wav, and mp3 formats

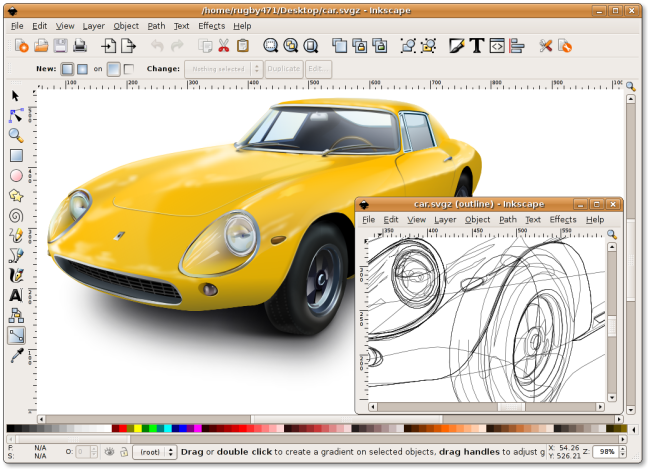
10.Inkscape
Whether you are an illustrator, designer, web designer or just someone who needs to create some vector imagery, Inkscape is for you! Inkscape is a free and open-source vector graphics editor; it can be used to create or edit vector graphics such as illustrations, diagrams, line arts, charts, logos and complex paintings.